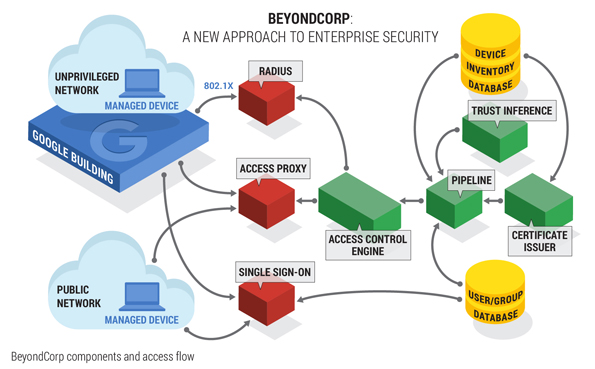
The Guiding Principles of BeyondCorp
Google threw out tradition and reimagined what a security framework should look like to be truly effective in today's world of distributed teams, systems, and applications.
Perimeterless Design
Connecting from a particular network must not determine which services you can access.
Context-Aware
Access to services is granted based on what we know about you and your device.
Dynamic Access Controls
All access to services must be authenticated, authorized and encrypted.